15/08/2018
We leave evidence of where we've been and what we've done all over the place. From footprints to DNA, we seldom act without a trace. Our keyboards are no exception. I'm not talking just about fingerprints, DNA, food particles, or skin oils. I'm talking about heat.
I saw a movie or maybe a television show once where a character enters a building by entering a code on a keypad. Another character uses infrared-sensing binoculars to discover what keys had been pressed. It turns out that works on keyboards, too. If someone knows what keys have been pressed to enter a password, the space of potential passwords is narrowed significantly.
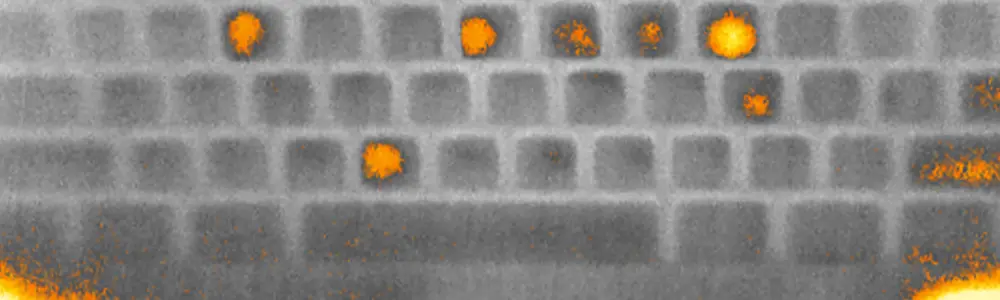
Three researchers from the University of California Irvine discuss these heat signatures in a new paper, Thermanator: Thermal Residue-Based Post Factum Attacks On Keyboard Password Entry. They used commercial thermal imagers to view keyboards after subjects used them to enter passwords. The paper is full of equations, graphs, and photos. There were some interesting results:
- Thermal "residue" is left on the keyboard for a long One image shows a keyboard twenty seconds after entering a password, and the keys pressed are clearly visible.
- Because touch typists rest their fingers lightly on the keycaps, there is significant noise - heating of keys not pressed. Hunt-and-peck typists left clear thermal residue.
- One subject with Acrylic nails typed with nail-tips instead of finger pads and left no thermal residue.
- Potential use of this as an attack vector is limited as the imaging left no reliable information about the order of the keys pressed.
In addition to the lack of key press order, it seems that there is limited information about repeated keys for "secure" (basically those without real words or repeated numbers) passwords. For instance, it does not appear that the signatures for 'food' and 'foood' would be significantly different. This supports the oft-given advice of repeating one or more characters in a "good" password.
The authors also compare the attack vector to others we discuss in Learning Tree's introduction to cyber security course, including shoulder-surfing and keyboard vibrations. I will add the information from this paper the next time I teach the course.
Finally, the authors do suggest some mitigation techniques. Their primary suggestion is to have the user press additional keys after the password which they call Chaff typing. This would warm other keycaps and make it more difficult to discern what was typed as a password. Other options include not using the keyboard to enter the password.
If you are interested at all in capturing passwords, I suggest you read this paper. For me it is yet another nail in the coffin of static passwords. Some form of varying passwords (an active token, or biometrics, for instance) would also mitigate this attack and many others. Readers of my posts here and participants in classes I teach know of my disdain for static passwords. Hopefully, this will encourage more research into practical alternatives.


